Uncover hidden threats. Understand your attack surface. Prioritize remediation efforts.
Every computer network is comprised of devices such as switches, routers, access points, cameras, printers, computers, servers, storage devices, and many others. With the rise of IoT (Internet of Things), we are seeing a further explosion of connected devices that often rely on the same networks our traditional systems connect to. Typically, a device will have embedded software that enables it to function. Additionally, the device will require configuration via human interaction in order to participate in the network and carry out tasks it was designed for.
It is typically in these two givens that bad actors find flaws that allow the compromise of a certain device or system. Compromises vary, but many allow for remote code execution, data theft, or availability impact. If a particular system can be accessed via the Internet, nearly any bad actor can attempt a compromise. According to the 2020 Verzion Data Breach Investigations Report, 30% of breaches involved internal actors. This emphasizes the importance of internal and external scanning.
Manufacturers, developers, threat intelligence groups, white hats, and others often discover flaws. Other times, bad actors may find and exploit flaws first, and the industry must react to them. Software updates, firmware updates, patches, workarounds and others may then be released which can mitigate the attacks, however many organizations are not taking the necessary steps to uncover and fix these flaws throughout the network on a continuous basis.
The National Vulnerability Database tracks and contains information related to vulnerabilities such as severity, links to vendor advisories and more. The number of high and medium vulnerabilities have increased steadily starting in 2017:
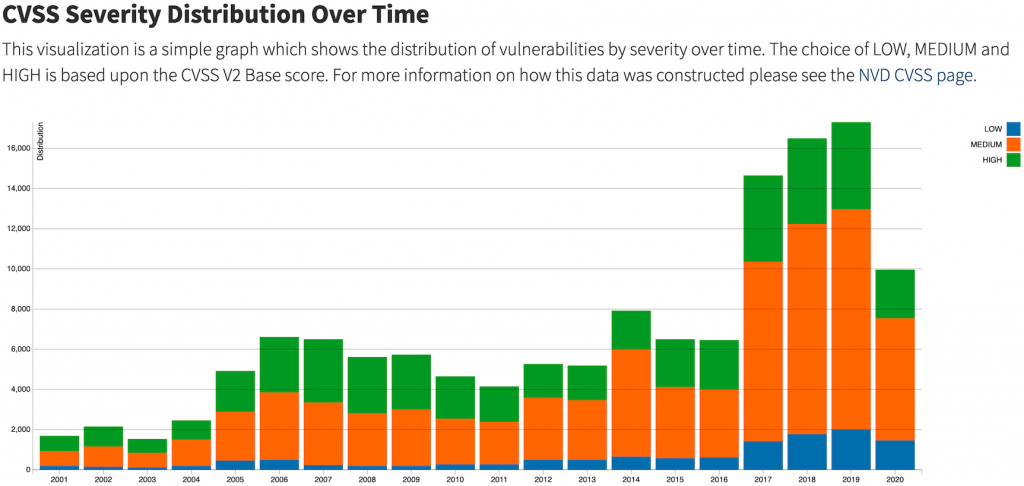
NVD – CVSS Severity Distribution
Methodology
Bound Planet offers various options for addressing this security control. Ideally, we work with our clients to build a continuous vulnerability management program where internal and external scans run on a periodic basis, vulnerability reports are provided, and a remediation plan is formed. Over time, attack surface can be observed and reduced, and newly discovered flaws can be quickly pinpointed. Additionally, prior to introducing any new production system, a scan should be run and any associated software or configuration should be updated so that a secure configuration exists from the onset. Bound Planet utilizes the industry leading Nessus Professional vulnerability scanning and assessment tool as the basis for scanning and reporting.
Application to frameworks / compliance
By working with Bound Planet to conduct regular vulnerability scanning and assessments, organizations can satisfy the following requirements:
- CIS 3.1: Run Automated Vulnerability Scanning Tools
- CIS 3.2: Perform Authenticated Vulnerability Scanning
- CIS 3.6: Compare Back-to-Back Vulnerability Scans
- CMMC RA.L2-3.11.2: Scan for vulnerabilities in organizational systems and applications periodically and when new vulnerabilities affecting those systems and applications are identified.
