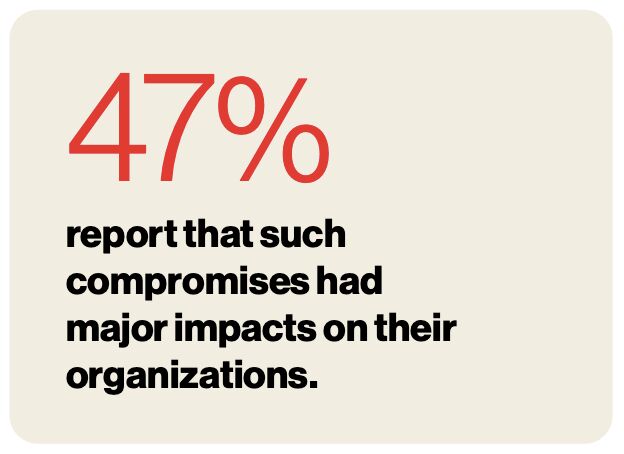
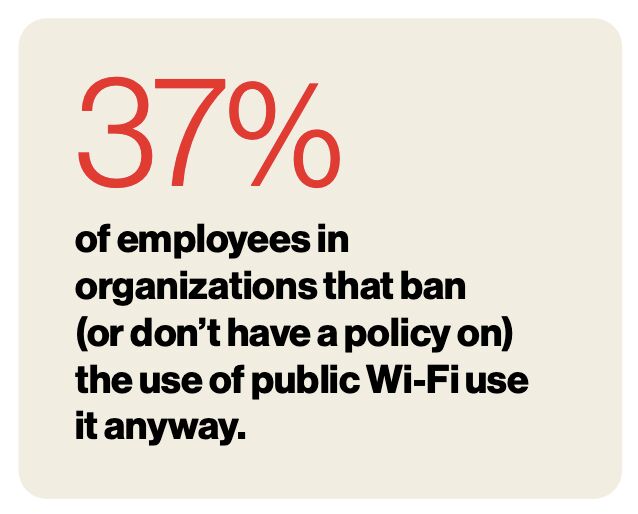
Do you allow mobile devices/compute platforms to connect to your business resources (365, wireless network, etc.)? Don’t let the cybersecurity considerations here go unaddressed.
I really appreciate the Verizon Business reports we have available when it comes to influencing how we might go about defending different areas of business technology. I have taken a couple snips from the 2024 Mobile Security Index. In our own consulting practice, I am seeing the challenges many organizations face reflected in this report.
Solutions here can be difficult to accept: costly, functional impacts, additional overhead, device ownership challenges…however, there are some common starting points:
- Do you have you open communication to discourage the pursuit of shadow IT?
- Have you developed a policy so your employees know what is expected?
- Do you provide training so your employees know how to recognize threats related to mobile device use?
- Have you reviewed your cloud provider’s built-in settings (if any) for management of mobile device connections?
- Have you made sure to move away from any vulnerable default configurations?
- Have you reviewed your wireless network configuration to ensure networks are correctly separated, strong authentication is enforced, and strong encryption has been enabled?
Want to strategize on how to address mobile and IoT security? Contact us for a free consultation!