Cybersecurity is a growing concern for businesses of all sizes. With the increasing sophistication of cyberattacks, it is more important than ever to take steps to protect your systems and data.
One of the most effective ways to protect your business from cyberattacks is to prioritize remediation of known exploited vulnerabilities. The CISA Known Exploited Vulnerabilities Catalog is a great resource for identifying these vulnerabilities.
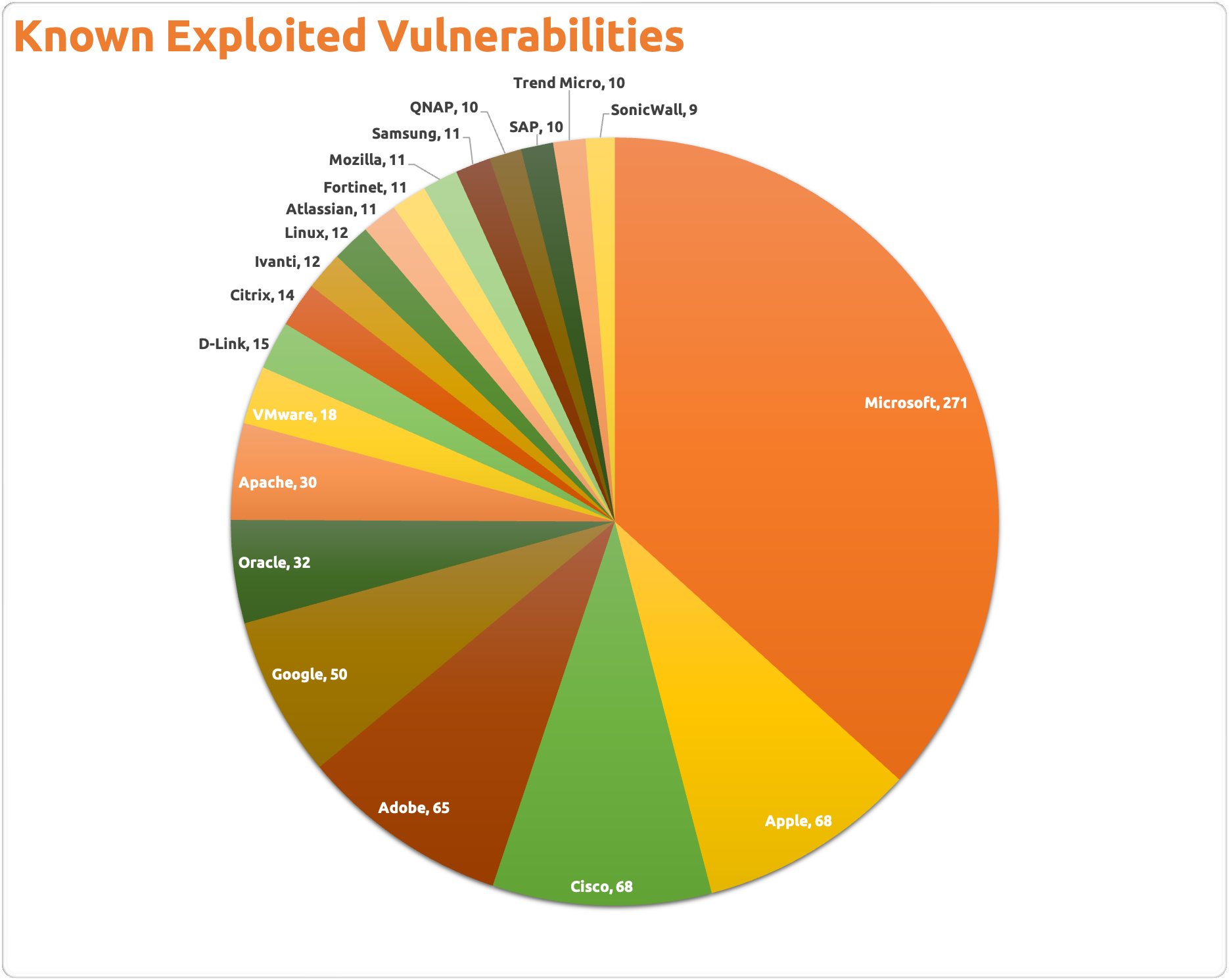
Here is a sampling from the KEVC as of 11/8/2023 illustrating vendors with known exploited vulnerabilities:
According to Binding Operational Directive 22-01, “Less than 4% of the total number of CVEs have been publicly exploited. Of those 4% of known exploited CVEs, 42% are being used on day 0 of disclosure; 50% within 2 days; and 75% within 28 days.”
This means that it is critical to remediate known exploited vulnerabilities as soon as possible. Failure to do so could put your business at risk of a cyberattack.
Here are some tips for prioritizing vulnerability remediation:
- Identify the vulnerabilities that are most likely to be exploited. This can be done by reviewing the CISA Known Exploited Vulnerabilities Catalog and other vulnerability databases.
- Prioritize vulnerabilities that affect critical systems. These are systems that are essential to your business operations.
- Remediate vulnerabilities as soon as possible. The longer a vulnerability remains unpatched, the more likely it is to be exploited.
CISA Known Exploited Vulnerabilities Catalog: https://www.cisa.gov/known-exploited-vulnerabilities-catalog